News & Perspectives
At Excite Cyber, we have bought together three of the leading names in Australian technology services – VITCS, Brace168 and Excite IT to deliver comprehensive and tailored solutions that meet your business objectives.
As such, some blogs and perspectives may retain their prior branding.

Protect your Microsoft O365 tenant
An organisation’s Microsoft 365 tenant is susceptible to many external and insider threats when not properly configured. At every level of licensing there are at

Why is penetration testing important for your business
Do you believe your data is secure? Do you believe your IT infrastructure is safe? Are your web interfaces hardened? These are just a few

3 Key Considerations When Creating a Cyber Security Policy
How should your organisation respond if a cyber security incident occurred? What is the current process for your employees when setting up passwords to ensure they follow

Top 7 Crucial Steps for Digital Transformation
Top 7 Crucial Steps for Digital Transformation Throughout the last couple of years we have witnessed changes in how traditional management, operations, and leadership roles

Hacks – October 2022
September saw a significant number of cyber breaches with Uber, Rockstar Games and Optus all impacted within a week. The attack methods observed in these

Hacks – Authentication
Authentication is a prominent aspect of cyber security as it is end user facing and is generally the first step to access most systems. A

Who Has Access to your Company Data?
Whether you own a business, are an individual or are part of a Government sector, chances are you have faced the common challenge of keeping

Hacks – May 2022 – Follina Zero Day Vulnerability
Tips and Tricks to mitigate and prevent “Follina”: References: https://www.huntress.com/blog/microsoft-office-remote-code-execution-follina-msdt-bug?hstc=1139630.416896d61b0745d0044e9a03af7f82ad.1653955273132.1653955273132.1653955273132.1&_ hssc=1139630.1.1653955273132&__hsfp=3244405923&hsutk=416896d61b0745d0044e9a03af7f82ad&contentType=listing-page https://doublepulsar.com/follina-a-microsoft-office-code-execution-vulnerability-1a47fce5629e https://support.microsoft.com/en-us/office/preview-attachments-in-outlook-6f61e4ad-a93d-408c-bb3a-bc95107f66be https://threatpost.com/zero-day-follina-bug-lays-older-microsoft-office-versions-open-to-attack/179756/ https://www.reddit.com/r/msp/comments/v0tuvs/ms_office_vuln_polite_warning_about_nearterm/
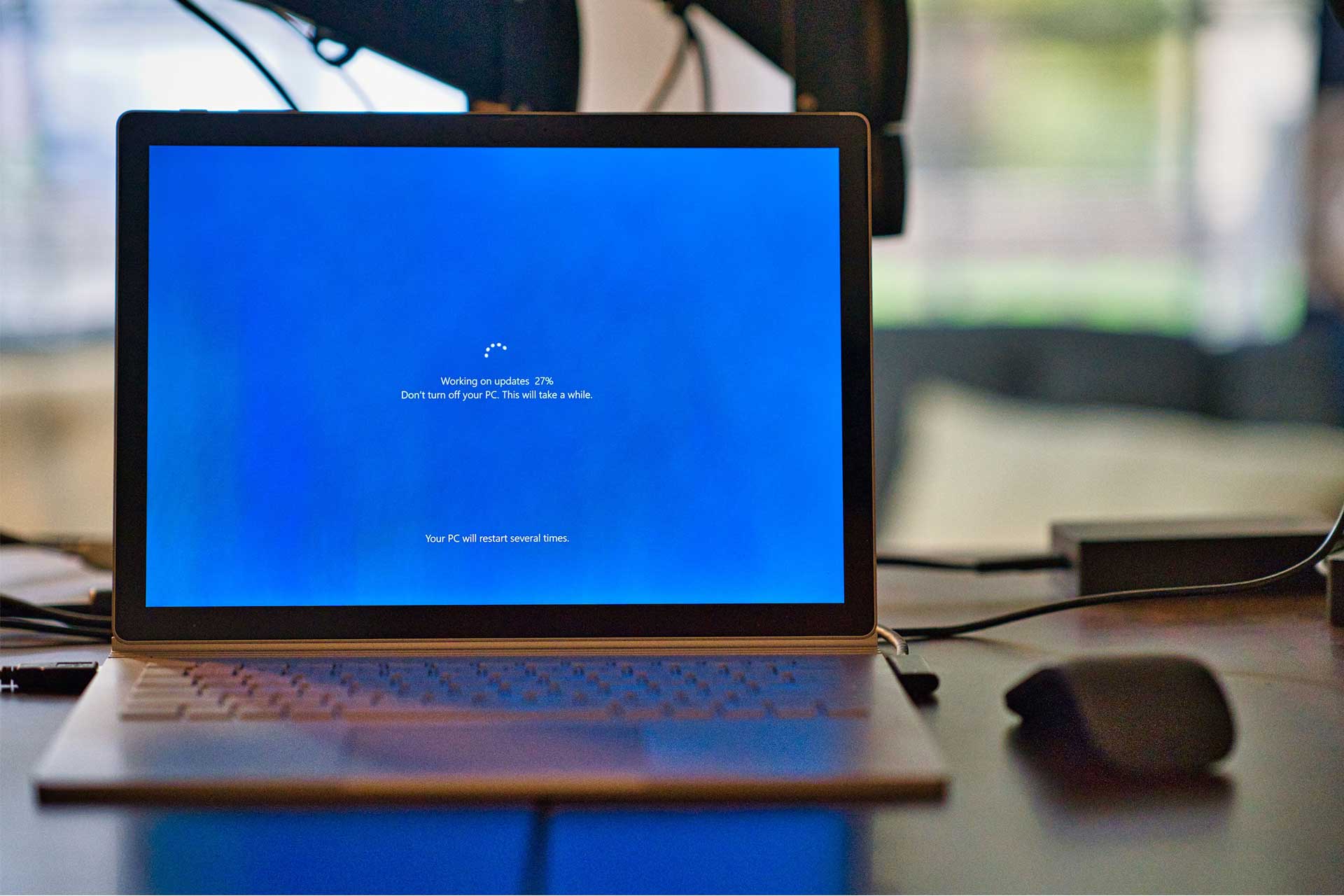
Hacks – Keep your Operating System safe
TIPS TO KEEP YOUR OPERATING SYSTEM SAFE Apple and Microsoft take great care in providing a safe and secure operating system for you to use

Encryption
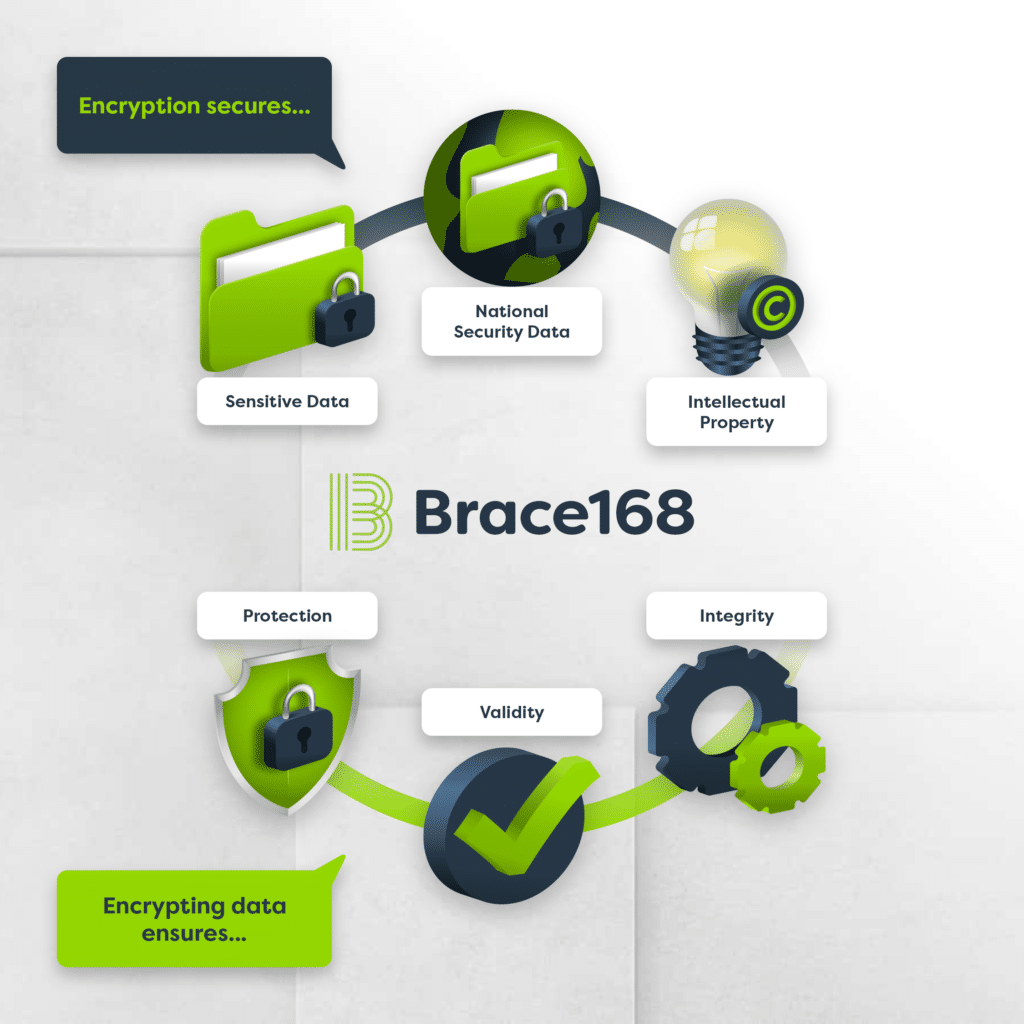
Encryption may be a topic that you give passing attention to in response to security advisories but otherwise little else. Rather than providing a summary
Encryption
Cryptography involves turning plaintext into ciphertext (encryption) and then turning ciphertext into plaintext (decryption). Data encryption protects confidentiality and safeguards data integrity. A cryptographic system

Common Vulnerabilities and Exposures
CVE-2022-21907: HTTP Protocol Stack Remote Code Execution Vulnerability Description: The exploit works by spraying an IIS server via several large GET HTTP requests and finishes with


