Allow Us to De-Stress and De-Risk Cyber Security
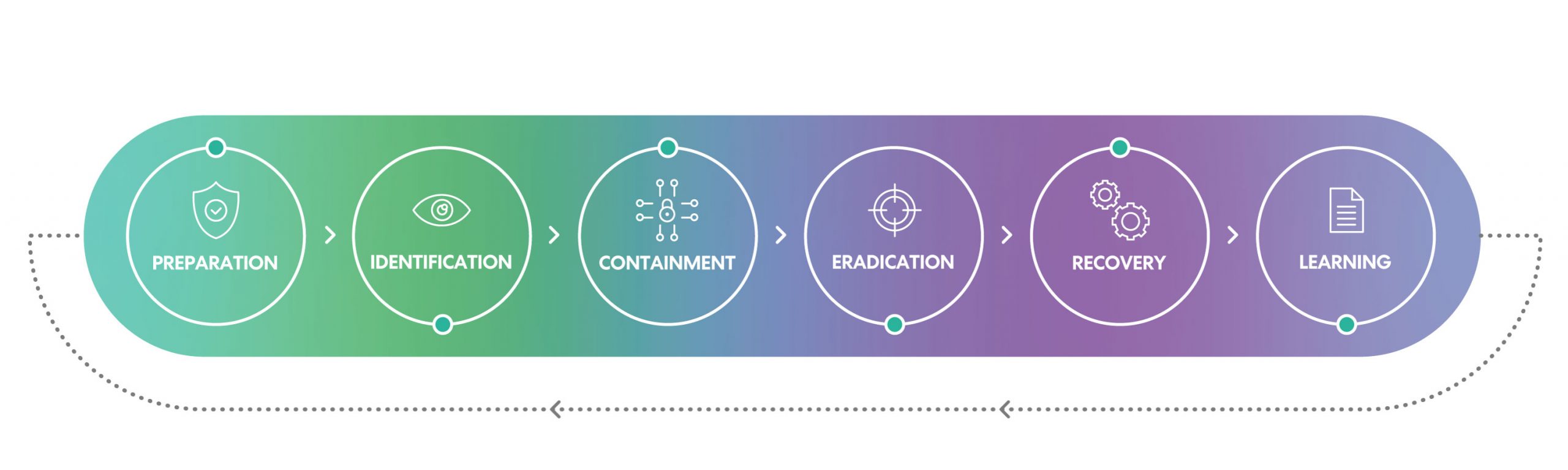
Excite Cyber follows a structured and widely accepted approach to incident response inspired by incident response frameworks developed by SANS Institute and NIST.
Excite Cyber IR service enables organisations to limit the impact of damages caused by security breaches and eradicate the root cause.
Excite Cyber Incident Response service addresses all six steps with activities and deliverables for each step as outlined below.

Who Needs This Service
Excite Cyber utilises ConnectWise as our project management tool and practices industry standard project management methodologies according to Project Management Professional (PMP) guidelines. Excite Cyber will provide regular project status updates and effective communication via email. Project progress meetings will be held on regular basis from order placement until onboarding completion.
Excite Cyber is focused on relevant cyber security outcomes, especially working with standards such as ISO27001, NIST and CREST, all of which Excite Cyber is well versed and has built a solid detection and prevention service catalogue.
In short, this service is valuable for anyone who has an ongoing and proactive need to maintain a properly monitored and compliant IT environment.

What We Deliver
- Review existing Incident response processes and key systems.
- Populate the Excite Cyber IR Playbook.
- Educate Customer on IR processes.
- RACI.
- Gain understanding of customer systems.
2. Phase 1 – Incident Detection & Response Discovery
- Identify affected assets.
- Review of high-level incident log.
- Identification of key users and or business systems impacted.
-
Network segmentation and edge
- Public facing critical business systems.
- Identify SaaS / PaaS platforms.
- Identify Remote access environment.
- Review current controls of identified systems impacted during incident.
- Create/implement communication plan.
- Brief Analysis of artefacts.
- Check identified compromised accounts PaaS\SaaS logs.
- Install Incident Response tool on limited number of devices.
- Check Event logs for authentication failures.
-
Define SoW for Phase 2
- Action plan
- Cost estimates
- Business downtime estimates
- Implement actions defined in SOW.
- Developing a detailed understanding of the scope and nature of the attack.
- Identifying and assessing the attacker’s tools, techniques and procedures (TTPs).
- Developing indicators of compromise (IOCs) and hunting for the attacker’s presence elsewhere across the network.
- Leveraging cyber threat intelligence to search for more information about that attacker, such as their affiliations, technical capabilities, history of previous attacks and other useful data points to aid in threat assessment and response efforts; and
- Provide advice and guidance to the recovery options for the Customer as required.
- Monitor for continued activity.
- Identify areas for improvement.
The Benefits to Your Business
IR Readiness
The Incident Response Team will understand your application architecture, cloud infrastructure, and database system and help strengthen incident response readiness.
IR Playbook
Incident Response Playbook will give a detailed insight into how the system will get audited and the processes and procedures followed while handling a security breach. It also improves the knowledge of threat detection and helps build reactive responses towards the threat.
First Responder Training (optional)
First responder training as a part of the Incident Response Retainer services will help your IT/cybersecurity team with an awareness of the evolving threats and proactive steps towards handling cyberattacks.
Simulated Attacks (optional)
Understand cyber vulnerabilities and identify the security gaps with simulated attack exercises. State-of-the-art incident response technologies put enterprise defence to test against evolving threats.
About Excite Cyber
We are cyber, technology and business experts who asked ourselves, what would the world look like if you could be truly fearless with your business, and what if the very best cyber expertise could be integrated into robust, outcome-focused technology solutions?
Our approach is to be deeply consultative and deliver pragmatic and strategic services that work for your business. With an uncompromising approach to cyber security, we deliver solutions that will get you excited about the potential for technology all over again.

Our Latest Perspectives
Australia Will Be A Leader In Quantum Computing: Why This Matters For Cyber Security
Quantum computing represents the next big “moon landing” moment for technological advancement. When it happens – and it will, with researchers getting ever closer to the big breakthrough – it will revolutionise industries and redefine how we engage with computing.

Why small businesses should see cyber security as a catalyst for innovation
Explore the escalating cyber security threats small businesses face and discover eight cost-effective steps to bolster IT security and foster innovation without fear.

Should You Pay The Ransomware Demand?
Ransomware news seems never-ending, but the most recent example is particularly pertinent to the subject: The Indonesian government refused to pay the ransom after a

Get Started with Excite
We are ready to collaborate with you every step of the way to protect your business and enable you to benefit from decades of experience in providing managed services.
To get started, schedule a complimentary call using the form below today.

Frequently Asked Questions
IR Readiness ensures that the Incident Response Team is familiar with your application architecture, cloud infrastructure, and database systems. This knowledge is crucial in strengthening your organisation’s incident response readiness and resilience against cyber threats.
Yes, there are optional services such as First Responder Training, which raises awareness of evolving threats and proactive measures, and Simulated Attacks, which help identify security gaps and test enterprise defence against evolving threats.
The Learning phase, often referred to as ‘Lessons Learned’, is vital for continuous improvement. After an incident, the IR team reviews what happened, what was done to respond, and how the situation was handled. Insights gained from this review help refine the IR plan and improve security measures to prevent future incidents.
Containment aims to limit the spread of an incident and prevent further damage by isolating affected systems. Eradication involves eliminating the threat from the environment, such as removing malware and fixing vulnerabilities that were exploited during the incident.



