Hacks – October 2022

September saw a significant number of cyber breaches with Uber, Rockstar Games and Optus all impacted within a week. The attack methods observed in these breaches were MFA fatigue attacks and a vulnerable public API in the case of the Optus breach. MFA fatigue attacks are becoming a more frequently used MFA bypass technique, where […]
Hacks – Authentication

Authentication is a prominent aspect of cyber security as it is end user facing and is generally the first step to access most systems. A poorly configured authentication layer can be the difference between a secure application and a complete breach. While thankfully not all exploits are critical, access to a system administrator’s account can […]
Hacks – May 2022 – Follina Zero Day Vulnerability

Tips and Tricks to mitigate and prevent “Follina”: References: https://www.huntress.com/blog/microsoft-office-remote-code-execution-follina-msdt-bug?hstc=1139630.416896d61b0745d0044e9a03af7f82ad.1653955273132.1653955273132.1653955273132.1&_ hssc=1139630.1.1653955273132&__hsfp=3244405923&hsutk=416896d61b0745d0044e9a03af7f82ad&contentType=listing-page https://doublepulsar.com/follina-a-microsoft-office-code-execution-vulnerability-1a47fce5629e https://support.microsoft.com/en-us/office/preview-attachments-in-outlook-6f61e4ad-a93d-408c-bb3a-bc95107f66be https://threatpost.com/zero-day-follina-bug-lays-older-microsoft-office-versions-open-to-attack/179756/ https://www.reddit.com/r/msp/comments/v0tuvs/ms_office_vuln_polite_warning_about_nearterm/
Hacks – Keep your Operating System safe

TIPS TO KEEP YOUR OPERATING SYSTEM SAFE Apple and Microsoft take great care in providing a safe and secure operating system for you to use in everyday life. There are several things you can do to keep everything working correctly and to make sure you stay safe. Also, your IT Team are there to support […]
Encryption

Encryption may be a topic that you give passing attention to in response to security advisories but otherwise little else. Rather than providing a summary of the state of the art of encryption technologies, this article will cover four practical applications of encryption that might have gone unnoticed recently. Encrypting mobile endpoints (BitLocker for Windows, […]
Encryption
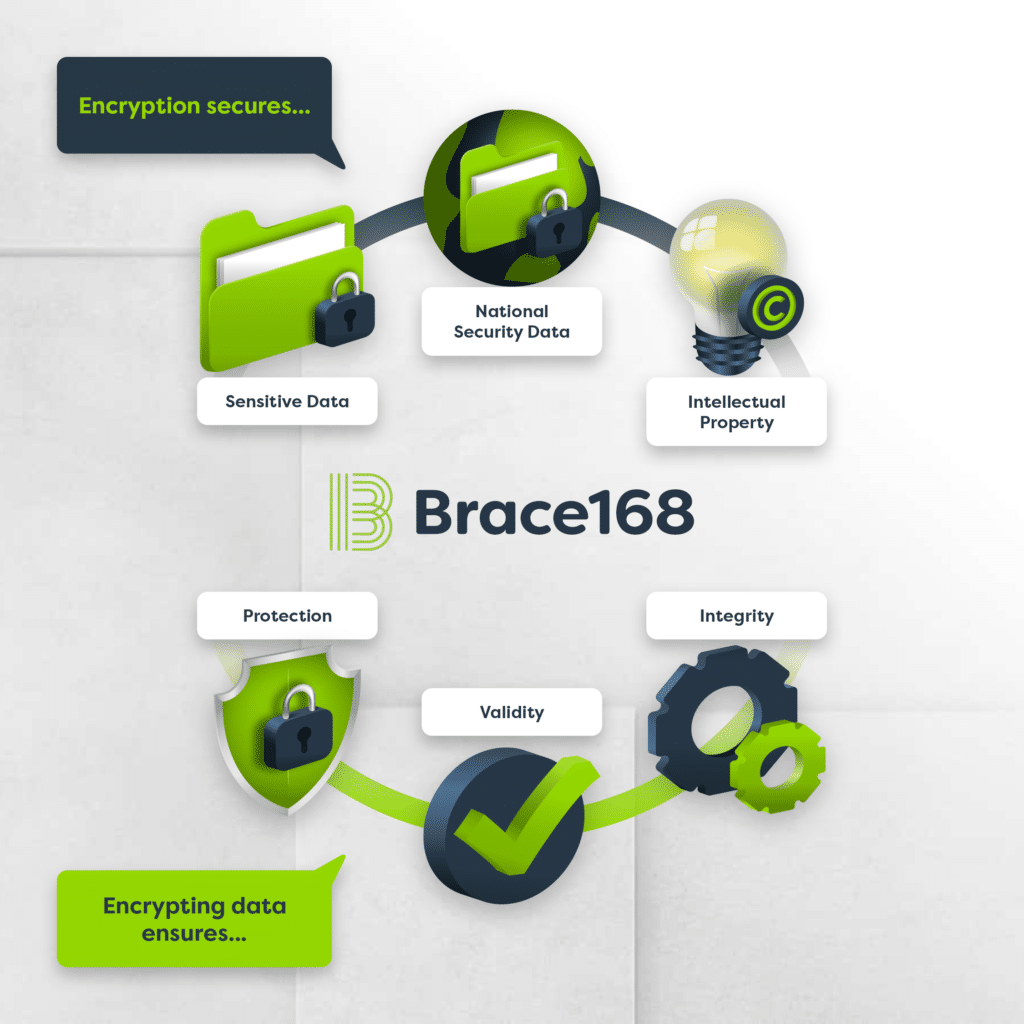
Cryptography involves turning plaintext into ciphertext (encryption) and then turning ciphertext into plaintext (decryption). Data encryption protects confidentiality and safeguards data integrity. A cryptographic system provides a method for protecting information by disguising it in a format that only authorised systems or individuals can read. Cryptography is generally thought of as being good at: Criminals […]
Common Vulnerabilities and Exposures

CVE-2022-21907: HTTP Protocol Stack Remote Code Execution Vulnerability Description: The exploit works by spraying an IIS server via several large GET HTTP requests and finishes with a malformed HTTP request. Mitigation: Windows Server 2019 and Windows 10 version 1809 are not vulnerable by default. Unless you have enabled the HTTP Trailer Support via EnableTrailerSupport registry value, […]
Common Vulnerabilities & Exposures June 2021

Vulnerability 1: D-Link Insufficient Credential Protection (7.2 High) Description: D-Link is affected by a credential exposure vulnerability. Credential exposure allows an attacker the ability to access credentials without any hindrance at all, granting them access to critical systems. In the case of D-Link, credentials are insufficiently protected in D-Link DIR-2640-US 1.01B04 and in D-Link AC2600 (DIR-2640), credentials […]
Common Vulnerabilities & Exposures May 2021

Vulnerability 1: UPDATED Microsoft Exchange Server RCE (9.8 Critical) Description: Microsoft Exchange Server has a new remote code execution vulnerability (RCE). These RCE’s enable an attacker to gain allow an attacker to execute code on a computer via a file that could be sent via email or delivered by USB and when downloaded can deploy […]
Common Vulnerabilities & Exposures

Vulnerability 1: DotCMS Remote Code Execution Vulnerability (10.0 Critical) Description: A Remote Code Execution (RCE) vulnerability exists within DotCMS v5.2.3. An RCE attack involves an attacker executing code from an external location without, technically, physically operating on the compromised device. In DotCMS’ situation, an attacker is able to specially craft a HTTP POST request, through the […]


